Last updated on January 19th, 2026 at 03:21 am
I mean, I will be frank- I was spending several years believing that my antivirus subscription was protecting my system. You are used to it: green checkmark, your device is safe, all okay. Afterward, I began to investigate how contemporary online attacks really do their work and… well. The green checkmark did not pay off as I expected.
In this case, what I learned once I began reading about AI Endpoint Detection and Response (EDR) is that it is not merely an improvement of antivirus. It is an entirely new method of security which presupposes that your antivirus has already not worked. And honestly? The latter assumption is at least more sensible than being in denial and thinking that a scan every week will identify everything.
In case you are technical, in the IT field, or simply need to know why cybersecurity has changed so radically over the last few years this is the breakdown that I would have liked to be informed of in the past.
Table of Contents
When Antivirus Stopped Being Enough
The traditional antivirus performs a single task: comparing files on your computer system with one huge database of known bad stuff. That’s it. Scans occur periodically, i.e. perhaps weekly, perhaps when you happen to think of scanning one, and when the code signature is found to match one in the database it is flagged.
The issue? 81 percent of the modern attacks do not involve conventional malware any longer. They exploit proper tools already on your system, PowerShell, Windows Management Instrumentation, that which is supposed to be there. These tools are being executed by your antivirus that believes, “Nah, that is natural. Meanwhile, attackers are taking advantage of those very tools to steal credentials, navigate between systems and steal data.
I experimented with this using certain tools of penetration testing (it was legal, but in a controlled setting). I was able to issue commands, form persistence systems, and pretend to steal data, and all the time with my antivirus on there displaying that comforting green checkmark. None of the things I did corresponded to a recognized malware signature since it was not malware that I was using. The operating system was the one I was utilizing.
The Day I Realized My Antivirus Was Basically Useless
The time off-limits was to read about fileless attacks. These do not save any executable codes to your hard disk at all they run fully in memory. Antivirus scans files and since you do not have any files to scan you can see the issue.
Next, there is polymorphic malware which recodes itself each time it propagates. The same functionality, totally different signature. The antivirus is searching the previous threat, but the current one is of a new form.
The antivirus model- scan files, match signatures, block known threats were indeed found to be fundamentally inadequate by 2026. Not that they were not trying hard but because the whole strategy presupposes that the attacks resemble an old scenario that we have encountered.
What Actually Is EDR (Without the Corporate Jargon)
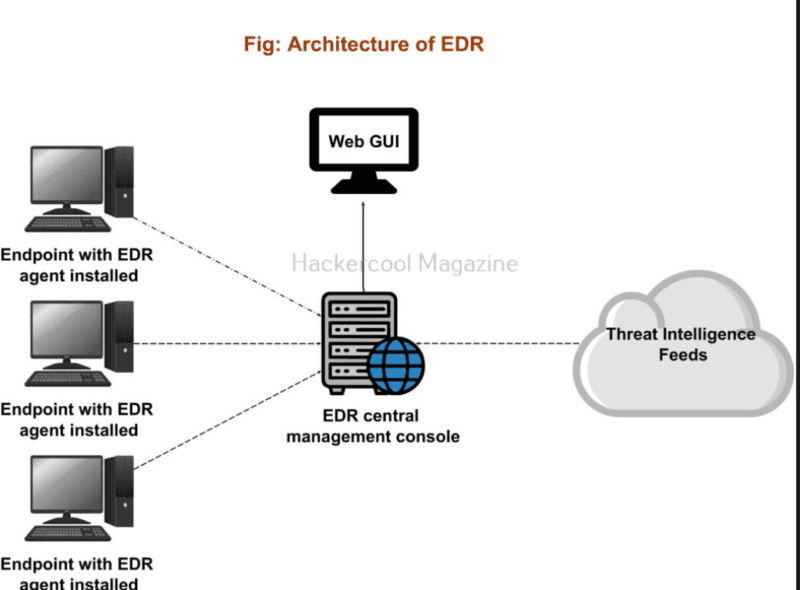
EDR reverses the security model. Servers will use EDR instead of asking whether a particular file is bad, and will use the query is this behavior suspicious?
All your network devices, such as laptops, servers, workstations, are installed with an agent that always keeps an eye on what is going on. There is not only the scanning of files, but also the observation of processes run, monitoring network connections, noting file modifications, registry change logging. Everything.
Upon first hearing continuous monitoring I envisioned some kind of dystopian surveillance nightmare. However, the point is as follows: your employer does not monitor you using Reddit at work (there are other tools to do so). It is observing processes at the system level that are usually not touched by users of that system, the sort of stuff that the user only sees when the system is being probed or a network robot is churning across the network.
Think of It Like This: Security Cameras vs. Motion Detectors
Antivirus is almost a motion detector by your front door. It notifies when something exceeds on a particular threshold- a threat signature. But when the burglar enters by a window, or breaks the lock, or persuades somebody to allow him to enter? It is not known to the motion detector.
EDR is the cameras that are omnipresent, which are always recording. It does not wait till something passes some threshold. It observes all, defines what normal will appear like in your place of surroundings, and indicates the abnormalities. At the moment, when a person makes that lock, EDR notices the suspicious use of tools, the strange time, the unusual access scheme, although the necessary person may have valid requirements.
This transition took place over time. 2014-2020 Early EDR systems used rule-based detection. The security teams would come up with rules such as alert on the running of PowerShell with an appeal to the encoded commands at three in the morning. Antivirus was not as effective, still, attackers mastered how to bypass certain regulations within a very short period.
Then AI-powered EDR arrived. Rather than clearly defined rules, machine learning models take into account billions of events, determine a behavioral threshold on a per-user or per-system basis, and detect abnormalities with no one having to instruct them on precisely what they are supposed to examine.
How EDR Actually Works: The Always-Watching Approach
The immediate detail I found when launching a test EDR agent on my personal computer, was the amount of data being generated by the EDR. All processes began to work, all network connections were made, all files were modified, tracked, reported, and uploaded to EDR platform to analyze and examine them.
This isn’t lightweight. EDR produces huge volumes of telemetry. It could be as much as terabytes of endpoint data in a day in one organization. However, it is that data that makes the entire system work.
What EDR Sees That Antivirus Misses
That is what really surprised me, here is what happens when I open a Word document: dozens of system events are evoked. The EDR agent records:
- How the file was opened.
- Did any of the spawned (like macros launching PowerShell) processes use the child process?
- Document load This is a network connection which starts when a document is loaded.
- Registry modifications
- File system changes
Word document is scanned once by antivirus which checks whether the signature of the file is identical with known malware and proceeds. EDR observes the whole process of what happens after opening the document.
However, when I tried a malicious macro (controlled environment again), my antivirus virus did not raise any red flag- the macro was never a known threat. But the suspicious activity did not escape EDR as quickly as possible: Word had started a PowerShell process with encrypted instructions trying to have connections to the external infrastructure. That is not a typical course of action, although each single piece of it can be considered a valid part of Windows.
The Four Things EDR Tracks Non-Stop
Process Execution: any program which executes, and also its creator (the parent process) and causor (child processes). Abnormal parent-child processes even such as Microsoft Excel setting up cmd.exe are immediate warning signs.
Network Connections: In which directions data is traversing, who is initiating the data transmission and is it being sent to correct destinations. Background process randomly connects to IP addresses in jurisdictions where your company does not ever perform its activities? Worth investigating.
File Modifications: What is being created, deleted, altered or encrypted. Ransomware usually encrypts files quickly on a variety of directories- a trend that EDR uses to identify regardless of whether the particular type of ransomware is of new type or not.
Registry Changes: Windows registry alterations such as creating persistence (to allow malware to survive a reboot) or that of turning off security functions. Software is changing the registry every minute, but some modifications, such as those to startup locations, warrant attention.
Detection That Actually Makes Sense
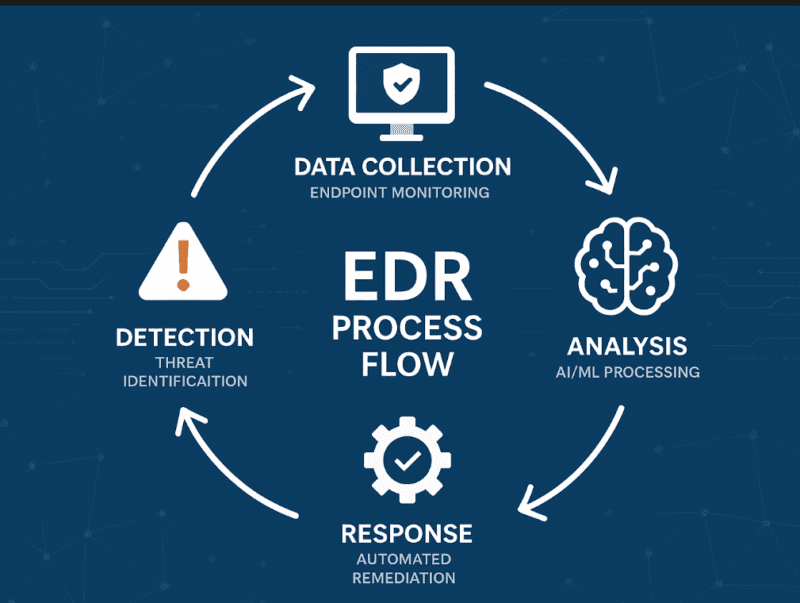
It is the analysis of all that data that provides the actual intelligence in EDR. It is upon this that Behavioral Analysis & Prevention layer comes in, and AI truly alters the game.
Behavioral Analysis & Prevention: Spotting the Weird Stuff
The traditional rule-based systems operate in the following way: A signal (process A does action B on condition C) in case of C. That suits well with known attack patterns, yet attackers simply vary the pattern in some ways.
Behavioral analysis does not follow the set rules. Rather it defines what normal is to each user, each system, each time frame. Executing high power level PowerShell commands at 3AM may be typical emergency maintenance by the system administrator. An underdeveloped programmer performing the same task? Most likely spooted credentials.
I viewed this show in a demonstrative setting. EDR platform was aware of the fact that there were users who consistently accessed certain files share at the expense of doing business. It was immediately reported by EDR when credentials used by one user were used to access entirely different shares at 2 AM, the shares which this user had not touched previously. The credentials were valid, the permissions to access were valid though the behavior pattern was incorrect.
Rule based systems find it difficult to do this contextual awareness. You would need thousands of rules to address all legitimate cases that may occur, and you would not address edge cases.
When AI Learns What “Normal” Looks Like
These machine learning models take all the historical data of your whole organization-users, departments, periods of time-and construct multidimensional baselines. They find non-linear and complicated relationships between things that they can not capture by human beings trying to use rules.
Anomaly detection with the help of autoencoders impressed me the most. These learning systems which are non-supervised compress representations of normal behavior, and these results are then measured against their fit to new activities. Reconstruction error so high, that is, the new behaviour does not fit the normal pattern, raises an alarm.
A good real-world analogy is process injection (injecting one process into the memory space of another process) which is a popular attack tool. This is not much done by legitimate software and is continual used by malware in order to masquerade within legitimate processes.
An auto-processor that is conditioned on your world finds out what processes interact with the memory in a regular way. Error of re-assembly peaks when the something begins to feed code to processes which it is not supposed to touch at all, even with the something being signed, and appearing to be, a legitimate binary. The EDR does not require a rule such as “block process injection by X. It simply perceives that the behavior that is being observed is very aberrant.
Hybrid CNN-RNN (a combination of Convolutional Neural Networks and Recurrent Neural Networks) has a detection accuracy of 97.3 and a false positive rate of less than 1%. Compare this with traditional rule-based systems that reached 45% false positives, and this explains the need of AI.
AI Threat Detection Explained (Finally)
I have read dozens of articles on the topic of AI-driven security that is nothing but marketing spam. Now, to clarify, what is the situation where the EDR vendors claim to detect threats using AI.
Pattern Recognition Without the Patterns
Known Pattern matching Patterns that are known to the traditional pattern matching system malware signature, attack signatures, address of command and control servers. In no case are you detecting a pattern which is not in the database.
Even in the event that the type of attack is novel, AI-based pattern recognition acquires abstract features to identify malicious behavior versus benign activity. Consider it the following way: you have never seen me, but you can know that I am human since you have heard about the abstract characteristics of being human two arms, two legs, some proportions, some specific patterns of movement.
On the same note, the AI models study abstract characteristics of bad behavior. Some of the credentials theft indicators include the abnormal authentication trends, systems cross-sector movements, access of resources that the account does not frequently access, and data preparation in temporary directories. The malware tool used to steal the data may be entirely new, but the characteristics of such behavior are still the same.
I took this to test with capabilities of AI Threat Detection Explained in a sandboxed environment run a series of attack simulators with a series of custom scripts – nothing in any threat database. Most of them were intercepted by the Artificial Intelligence models of the EDR since the behavioral signatures were similar to the patterns of malicious work that have been learned.
How Machine Learning Spots Brand-New Threats
The worst nightmare of conventional security is the use of zero-day attacks i.e vulnerabilities which vendors are unaware of but exist. No signature, patch, prior knowledge.
AI-based EDR manages zero-days by utilizing behavioral based detection. It does not even have to be aware of the vulnerability that is exploited. It identifies the attempt of exploitation based on an unusual system behavior: an unexpected privilege escalation, a strange memory access pattern, processes that are communicating with each other in a way that they are not supposed to.
Long Short-Term Memory (LSTM) networks are better with regard to identifying slow-moving attacks that take either hours or days. When an attacker sets up persistence by placing automated tasks and then going silent only to be re-activated in a few weeks, the time features in an attacker arise, and LSTMs identify these time features with high accuracy even in conditions where a particular action is harmless.
Variational Autoencoders and Self-Organizing Maps are models of normal behavior distribution that are probabilistic. Alerting occurs when observed activity is not within such distributions, i.e. the probability of this being normal is too small. Such a practice picks off advanced targeted attacks that are specifically tailored to your environment, and generic threat intelligence would be of no use.
What Happens When EDR Catches Something
Detection should be accompanied with action. The fact that EDR responds as opposed to passive monitoring tools.
The Alert That Actually Tells You Something Useful
Conventional antivirus warning messages are of no good: “Threat detected: Trojan.Generic.12345. Great. What does that mean? What did it do? Where did it come from?
EDR notifications are in their full context: What user account was used, what processes were run, what network connections were made, what files were accessed and how all these can be connected. In addition to forensic information of the entire attack chain.
I compared notification on various systems. Antivirus: “Virus blocked are set, malicious file blocked.” EDR: User jsmith used his credentials to run PowerShell executable with coded commands,newly created a network connection to 45.33.21.109 (identified C2 infrastructure), tried to access the domain controller, and staged files to C:UsersPublicTemp. This is in keeping with known patterns of credential theft. Confidence: 94%.”
One knows that something bad had happened. The other informs you of the whole story.
Investigation Mode: Connecting the Dots Automatically
Modern EDR systems automate threat investigation with the attack rebuilding. The EDR platform will generate a mapping of the attack progression instead of having security analysts manually correlate dozens of systems logs over the course of hours or days.
I completed a demo in which I saw EDR re-creating an attack simulation displaying: phishing email initial macro run – credential theft – lateral migration to three systems – domain controller breakage – data exfiltration. The complete attack chain, represented automatically, time-stamped and pointed.
The machine learning algorithms compare events that occur at two or more endpoints at various moments in time and uncover trends that could never be uncovered by human investigation. When an attacker compromises his credential to log into and out of systems the individual action appears legitimate. But EDR identifies the pattern of co-ordination between endpoints and raises an alarm.
There is an addition of threat intelligence integration. Threat intelligence feeds automatically enter EDR platforms and locally generated events are then compared with global compromise indicators. The system identifies the connection between endpoint contacts infrastructure related to a threat in the known list- although the malware version itself may be novel.
Response Options When Threats Get Real
Non-response Detection Nonresponse is there just so long as there is attack. EDR makes the process of containment and remediation automatic.
From “Heads Up” to “Shut It Down Now”
Response capabilities are graduated in line with the severity of threats and maturity of an organization:
Mild Severity: Security personnel, isolate suspicious files, end suspicious processes. No effects to business activities.
Medium severity: Kill malicious processes, block network connections to attacker infrastructure, start forensic scanning of data Medium See stealth mitigation. Minimal user disruption.
High Severity: total network isolation of endpoint. The hacked device is completely severed–it is not able to contact other systems to communicate, is not able to exfiltrate data, is unable to be spread laterally. This is the get it out of business one.
In the current situation approximately 66 percent of systems operate autonomous threat response where EDR does their containment decisions independently without human approval. It takes down mean time to respond by hours and minutes, which is vital given that ransomware can encrypt a complete network within less than an hour.
An autonomous response was tested in a laboratory setting through the production of simulated ransomware behavior (rapid file encryption portly across directories). EDR agent automatically killed the process, quarantined altered files, and rather separated the endpoint only in several seconds, without human intervention.
False positives is its trade-off. Having an EDR wrongly isolate a production server with important business applications on it is, however, a strong blow to operational capabilities. This is the reason tuning and base creation are of high importance.
The Threats EDR Was Built to Handle
Current attacks are totally different to the viruses that arose in the 2000s. EDR has specifically developed to respond to these sophisticated methods.
Ransomware Detection and Prevention with AI
Ransomware Detection and Prevention with AI aids one of the most evident EDR value propositions. The peculiarities of ransomware practice are the following: quick encryption of files in several directories, frequently a particular type of files (documents, databases, back-ups).
AI models identify this trend despite the occurrence of a new variant of ransomware. The mass file-modifying action with the encryption produces the behavioral signature that triggers an alert before serious damages take place.
After the encryption of hundreds of thousands of files out of millions of files, I examined a case where EDR identified ransomware. The encryption behavior was detected within seconds on the basis of its rapid pattern. Manual detection would have seen the attack detected when massive encryption was already done.
It is very important to notice ransomware at an early stage. Preventing and finding it within the first few minutes will result in restoring 47 files out of backup as opposed to reconstructing your entire infrastructure.
Fileless Attacks and Other Sneaky Tactics
The fileless malware operates completely in memory- there is no contact with the disk, and thus file-based scanning will not detect it. These assaults use valid system applications such as PowerShell, WMI or Windows Script Host.
Under BE, EDR identifies fileless attacks by detecting the usage of processes. Upon launching PowerShell into execution where encoded commands are to be run, some form of unusual connection to the network is made, or accessing credential stores, EDR is raised irrespective of the presence of any malicious file.
The other area where EDR is strong is the credential theft. Attackers are also compromising valid accounts more often than malware installation. The credentials are stolen, they log in using them and they act on normal permissions.
Conventional security has no way of differentiating between a genuine user and an attacker who has expropriated credentials. EDR is able to identify access to atypical locations, access to unusual resources, outside-of-normal-hours access, unusual authentication patterns and this is possible through behavioral analysis.
Living-off-the-land attacks exploit already available tools on systems. These are noted by EDR as abnormal relations in the process between the parent and the child (Excel launching PowerShell), the presence of suspicious command-line arguments, and a variation to normal baseline use.
Making EDR Work With Your Other Security Tools
EDR does not overlay your existing stack of security- it inter-operates with it. The question is how smoothly.
SIEM Integration: Why It Matters
Security Information and Event Management (SIEM) systems combine logs within your infrastructure firewalls, servers, applications, cloud platforms, and correlate events to analyze them in a central location.
EDR echoes a rich endpoint telemetry create a cross domain correlation notification into SIEM. Once EDR pollutes abnormal process execution and SIEM detected abnormal network traffic on the same endpoint at the same time, you are more than capable of being confident that you are dealing with a real threat.
My setting involved an environment in which SIEM on its own produced thousands of alerts a day, the majority of which were harmless. EDR was brilliant at detecting endpoint anomaly but did not have network context. The combination was noise-filtering the alerts that seemed to occur in both endpoint behavior and network traffic were the only ones to be investigated on the spot.
The complexity is the integration complexity. Different vendors EDR and SIEM systems might necessitate specially written API, data format normalization, and sensitive work plan creation. Lack of integration results in data silos with your EDR view of the threats that your SIEM cannot detect and your SIEM view of the threats that your EDR cannot.
The SOAR is another level of automation, using SOAR platforms to automate response procedures. SOAR and EDR can be configured to activate playbooks when a threat is detected: isolate the endpoint, get a ticket, send alert to the security team, search threat data to find indicators and start a forensic investigation, all automatically.
Numbers That Actually Matter
All vendors of security have their claims that they are the best. Measures aid in reducing marketing and measure real performance.
Mean Time to Detection and Why Speed Counts
Mean Time to Detection (MTTD) is a metric that quantifies the time spent on dwelling on the threats in your environment without being detected. The average of industries is 181 days- attackers can act without being detected six months.
Organizations that employ EDR detect threats 82 times quicker than when they depend on antivirus, and MTTD reduces to hours or minutes (as opposed to days or weeks). Organizations that have developed threat hunting programs identify breaches within hours.
Speed is important in the sense that the length of time attackers spend in your network is directly proportional to damage. A six-month attacker can map your whole infrastructure, find out what is a crown jewel, develop a variety of persistence, and steal terabytes of data. An attacker that takes hours to be spotted does not affect much.
The measure of how fast you respond to and contain threats after detection is referred to as Mean Time to Respond (MTTR). EDR featuring automated responses minimizes the hours to minutes of the MTTR- which is important when ransomware is spread into a network at a swift pace, or data theft is under way.
According to organizations, that adopt Extended Detection and Response (XDR) which combines EDR components with network, cloud and email security, 53% decrease in MTTD and 59% decrease in MTTR of siloed EDR deployments was observed.
The False Positive Problem
This hurts the situation: most EDR implementations have a false positive of greater than 50-percent. Rates in some organizations are up to 80 percent -four out of five alerts are noise.
Security analysts become fatigued with alerts when the majority of them turn out to be benign. They begin to ignore new notifications since they have already been thorough in hundreds of false alarms. Then an actual danger is overlooked and an obliteration of noise is made.
False positives are significantly minimized by the AI-based EDR. CNN-RNN models reduce false positive rates by approximately below 1 percent under hybrid model, whereas rule-based systems record high false positive rates of 45 percent. That is why the difference between investigating 10 true threats and 100 false alarms and investigating 10 true threats and 2 false alarms is significant.
However, this is what vendors do not boast of: in the early stages of deployment when AI models are building baselines and getting to know your environment, false positives are on a high. The system is getting used to what is normal and therefore any thing that is slightly different raises alarm. This training stage is usually between 2-4 weeks and needs forbearance by security teams.
Detection rate – the proportion of genuine threats which have been detected successfully mean 97.3 percent using recent AI-EDR systems. It is drastically improved compared to the old-fashioned antivirus which is difficult against polymorphic malware, fileless and zero-day attacks.
Picking the Right EDR Solution
The EDR market is crowded. CrowdStrike, SentinelOne, Microsoft Defender for Endpoint, Palo Alto networks Cortex, Carbon Black- all the key vendors of security programs have an EDR platform.
What I Learned Comparing Different Vendors
I took my time to appraise a variety of EDR platforms (some of them by trial, others by demos and documentation). Here’s what actually matters:
Detection Capabilities: Is it an AI/ML or a rule-based detection? What is the alleged false positive rate? Is it able to identify fileless malware, credential theft and lateral movement?
Response Alternatives: Automated containment? Endpoint isolation? SOAR integration? What degree of autonomy would you like to setup?
Investigation Tools: Visualization of attack chains? Automated forensics? What level of manual correlation would be necessary?
Integration: Will it work with your existing SIEM, SOAR, and identity? Do you have some existing integrations or will you have to develop an API?
Explainability: Does it give a reason that it has flagged something or is it a black box? Only a small percentage of EDR vendors have Explainable AI (XAI), which, in other words allows viewing which particular types of behavior led to the threat scores. This is important in regulatory adherence and the generation of trust in mechanical decisions.
Performance Impact: What is the consume of CPU and memory by the agent? EDR works continuously on each endpoint, therefore, the utilization of the resources affects user experience.
Threat Intelligence: Does the vendor card their own threat research team? Routine update of threat intelligence feeds? Are they associating local incidence and global attacks?
Pricing is out of this world- starting at 30-100 dollars per endpoint/year with varying features and scale. A total cost of ownership is not only via licensing but also via implementation, training, continuing management and even possible professional services.
Agent vs. Agentless: The Real Differences
The majority of EDR solutions rely on the use of agents application software that is installed on each endpoint and tracks system activity and reports to a central platform. The agents are deep-visibility since they run at the OS level and has access to process execution, memory operations and system calls.
Foo (Agentless EDR) sniffs with the use of a network traffic and centralized logs and does not require software installation on the endpoints. The reason is that the technique is suitable when organizations are not able to place agents on specific devices (IoT devices, legacy systems, BYOD scenarios) or have issues with the performance impact of doing so.
The other is depth of visibility. Everything that occurs on the endpoint can be perceived by agents. The agentless methods deduce network traffic and available logs and are therefore not as informative as to what is actually happening at the system level.
I tried the two methods under varying conditions. The fileless attacks and in-memory malware detected by agent-based EDR would have been overlooked by agentless systems since there is minimal or no network traffic produced by such attacks. Agentless EDR was sufficient to identify network-based risks but it failed in regard to endpoint-based attacks.
To achieve a comprehensive coverage most organizations employ agent-based EDR to be complimented through agentless monitoring of those machines that cannot have the agent installed.
Is EDR Worth It in 2026?
Since I researched the actual functioning and testing implementation of EDR, and contrasted them with what was previously implemented in security measures, I found:
Provided that your organization deals with sensitive information, functions in a regulative sector or has a steady run of cyber criminals (at this point, everyone is obliged), EDR is no longer optional. In essence, the traditional antivirus is unable to counter modern attack methods, including living-off-the-land exploits, fileless malware, credential theft, ransomware with new signatures.
This is supported by the figures: 95 percent decreased cases of successful endpoint infections with a well-implemented EDR. Detection time reducing to months, then hours and then minutes. Reconstruction of attack chain that would take days of manual investigation occur automatically.
But properly deployed means something. EDR needs to be initially tuned (2-4 weeks), a combination with already established security tools, it also needs to be trained to the staff and optimized as your environment grows. Companies that use it as a set and forget solution are wasting their investment and get lost in false alarms.
The learning curve is real. Behavioral analysis, attack chains, and threat investigation cannot be fully learned using only the traditional IT administration skills. The resources I discovered and found free, OpenEDR Academy, EDR Internals offered by TrainSec, endpoint security training at Purple Academy may assist teams in building those capacities without expensive training.
In case of organizations that have already developed security operations, autonomous response features decrease the need of using manual investigation and provide timely containment. To less mature organizations, EDR guided exploration and forensic features assist junior analysts to interpret an assault and react suitably.
It is evident that EDR moves towards Extended Detection and Response (XDR) which amalgamates endpoint and network, as well as email and identity security into one consolidated platform.
Approximately, 80 percent of EDRs by 2027 will have the migration over to XDR because as organizations realize that the endpoint alone visibility fails to notice advanced attacks across various domains.
Verdict: the answer is yes to EDR. But it’s not a magic bullet. It is a platform security which needs to be invested into implementation, integration, and knowledge in order to extract its maximum worth. Those organizations that receive real security benefits in EDR are those who are treating it as a performance tool shedding light on its use that must be endlessly improved at the same time remaining a security tool to be put in place and forgotten.
The distinction between possessing EDR and possessing effective EDR is that your security team will be able to respond to the breach in hours rather than months. That disconnect is what will make the difference between you coming out of a dusty event and a disastrous compromise.
And honestly? With the revelation of the actual role of contemporary attacks, that green checkmark of the antivirus of yesteryear becomes even more superfluous than ever.
I’m a technology writer with a passion for AI and digital marketing. I create engaging and useful content that bridges the gap between complex technology concepts and digital technologies. My writing makes the process easy and curious. and encourage participation I continue to research innovation and technology. Let’s connect and talk technology!



