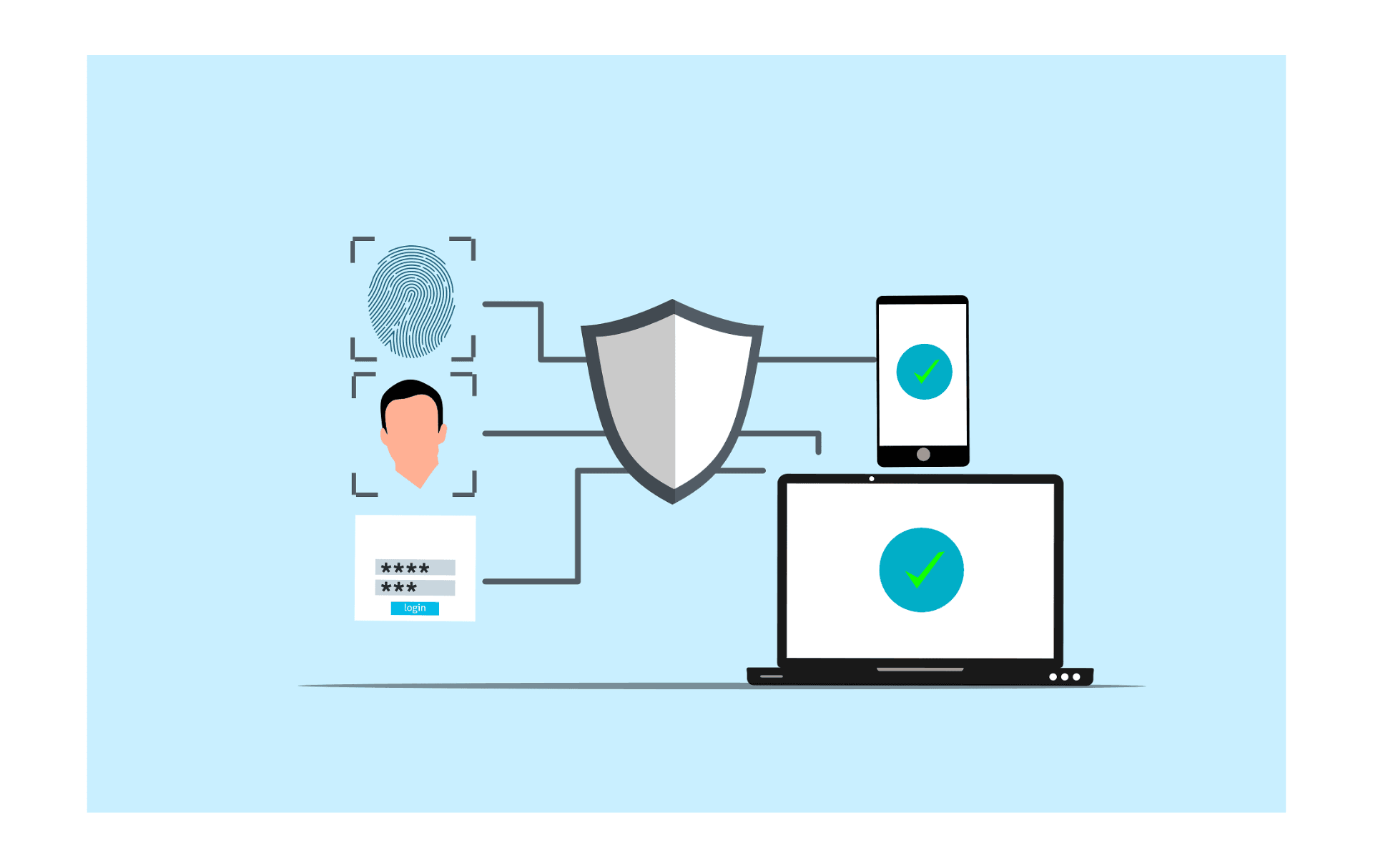
Last updated on December 30th, 2025 at 03:27 am
Here’s the thing, however, one day you are going to create a relatively simple logging-in page and the very next day people will start asking about SAML integration, OAuth processes; about MFA that is resistant to phishing. It’s a lot.
That moment of confusion? That’s where this started. Several weeks of assembling the puzzle of what is actually implemented in authentication modes and protocols (and why there are so many) finally lead to the breakdown that would have saved hours of head cleaning.
This is not just the memorization of acronyms. It is about being knowledgeable of the landscape to the point that when the next person is discussing WebAuthn or why you can never simply use passwords, you will actually have a clue.
Table of Contents
What even is authentication (and why is it so important)?
It is necessary to first clarify this: the protocols provide the response to the question, who are you. and authorization replies to the question of what can you do?
Imagine the following: you driver license identifies who you are (authentication). The bouncer who looks whether you are 21 years old to be in the bar? That’s authorization.
The distinction between authentication and authorization is important due to a lack of understanding, which results in security vulnerabilities in case they are mixed up. One such service is OAuth, which does not process authentication. As a non-OpenID Connect method of logging in? It is a typical thing to regret and create some actual issues.
That is the entire rationale of authentication procedures and techniques to authenticate identity. However, at this point, things get ugly: dozens of techniques exist to do it, and they all address various problems.
The Authentication Landscape: Why So Many Options?
The confusion in authentication is as follows: various contexts require various solutions.
Logging into a website? This is unlike when one is connected to corporate Wi-Fi. Accessing an API? Different again. Every scenario developed its authentication mechanisms and procedures throughout history.
Some key categories:
Certain network access protocols such as PAP, CHAP and EAP support Wi-Fi and VPN connections. It is older, they are more stable, and quite frankly not very exciting but they run enterprise networks all over places.
The costly passwords changed to cookies and a session and later to advanced protocols such as SAML and OAuth. Herein the sphere of the majority of contemporary misunderstanding.
The future of passwords is passwordless authentication platforms such as WebAuthn and passkeys. They are used to prevent phishing attacks that continue to defy passwords and even SMS codes.
The catch? All these are operated simultaneously by most organizations. Your business may be logging in Kerberos to Windows, SAML to enterprise apps, OAuth to APIs, and plain password forms may have their places all over.
That’s not bad architecture. It’s just reality.
Classic Techniques: Passwords, Sessions and Reasons Why They persisted.
The use of passwords is pervasive even though it is a very weak form of security. They are phished, re-used, breached in attacks, and brute-forced.
But this is the reason why they have not disappeared: they are simple. Users understand them. They are supported by all platforms. No more passwords, however, presents the challenge of account recovery, device switching, and the problem of losing users.
It was a little better with sessions and cookies. Upon logging in, your browser caches an encrypted session ID in a browser cookie. The server authenticates that ID with each request as opposed to requesting credentials on several requests.
The recent settings of the sessions make use of HttpOnly, Secure and SameSite to block JavaScript access and cross site attacks. Nothing big, but it is important to the security.
OTPs also incorporated a second option: authenticator application, SMS, or email codes. Stronger than passwords, though, it can be phished. SMS can be intercepted, the attacker will be able to steal codes or will be able to trick the user into providing the codes on counterfeit websites.
The pattern here? Each of the methods addressed certain issues and brought new ones.
Enterprise SSO: Organizations Requirement Unified login.
Optimized federated authentication was added to an enterprise environment: a single login to dozens of applications.
This is done with Kerberos and windows domains and corporate networks. It utilizes tickets and symmetric cryptography to verify identity by transferring no passwords in the network. It is effective, but it is complicated and limited mostly to intra-networks.
SAML 2.0 introduced single sign-on using the web. In most cases, when you issue a click on the “Login with Okta button or Sign in with the Azure AD, that is actually SAML underneath the carpets.
SAML is based on the XML to exchange identity assertion of an identity provider (IdP) and a service provider (SP). It is mature and it is used in B2B and it is not quite leaving any time soon- but it is also difficult to implement and debug.
The trick is that SAML is largely overlooked by newer applications in order to come up with more uncomplicated solutions, but older enterprise software runs on SAML. When it comes to comparing SAML vs. OAuth vs. OpenID Connect it is possible to refer to the circumstances under which they can be used but the gist of it? SAML overpowers current enterprise SSO.
OAuth and OpenID connect: The Modern Web Stack.
It is here that the greatest part of the present misunderstanding occurs.
OAuth 2.0 is an authentication framework – not an authentication. It allows applications to have access to APIs in your presence, without sharing passwords. When a mobile application requests to make a post to twitter, it is OAuth with a restricted access.
The trick: OAuth issues access keys to APIs. It does not mention the identity of the user.
Identity: OpenID connect (OIDC) is identity over OAuth. It adds the ID tokens and in fact they include user details: email, name, roles. That is what makes OAuth an appropriate authentication protocol.
New-fangled web apps are often written with PKCE Authorization Code flow (a security extension that prevents theft of tokens). The flow looks like:
- User clicks “Login”
- Identity provider/App redirects to identity provider.
- User authenticates there
- IdP causes a code to be redirected back.
- Tokens are coded according to the app exchanges.
- The application uses tokens in order to get access to user details and APIs.
Sounds simple. Practically, it can be said that there are pitfalls: redirect URI manipulation, leakage of the token of use, CSRF attacks and mix-up vulnerabilities during which attackers deceive the flow. The JWTs and refresh tokens are discussed as token-based authentication in such cases.
Why does this matter? Due to the OAuth and its OIDC, the typical modern authentication: social logins, API access, mobile app, microservice, etc. works. Making a wrong choice implies security holes.
WebAuthn and Passkeys: The Anti-Phishing Future.
This move is the largest change currently: leaving the concept of knowing (passwords) in favor of having (cryptographic keys).
WebAuthn is one of the standards within the browser and allows sites to utilize cryptography based on public keys to log in. Rather than entering a password, you can unlock a private key with your fingerprint, face or device PIN. The public key is the only one that is displayed on the site.
The protocols that link physical security keys such as YubiKey itself are WebAuthn, but the covering name is FIDO 2.
Passkeys are user friendly: synced WebAuthn credentials that are compatible on your devices. They are now supported by Apple, Google and Microsoft.
Their importance: passkeys are committed to particular websites. Although somebody dupes you to go to fake-amazon.com, your passkey would not work there, it would work in actual amazon.com only. Going after nothing to phish or steal.
The challenge? Users also require backup facilities to lose and recover devices. Passkeys are not required in most apps currently as a backup to passwords. Nevertheless, the trend is apparent: the passwordlessly authenticated mode will become a standard in the future.
Knowledge Base: When to use which protocol: Practical map.
This is the mental model that is of use:
| Scenario | Protocol/Method | Why |
|---|---|---|
| User login to web/mobile app | OpenID Connect | Modern, JSON-based, well-supported |
| Enterprise B2B SSO | SAML or OIDC | SAML for legacy, OIDC for new |
| API access delegation | OAuth 2.0 | Designed for this exact use case |
| Service-to-service auth | OAuth Client Credentials or mTLS | Machine identity, no user involved |
| Phishing-resistant login | WebAuthn/Passkeys | Cryptographic binding to origin |
| Network/Wi-Fi access | EAP variants | Enterprise wireless standards |
It is not the trick to memorize this table. It is the realization that authentication methods and protocols will solve various issues drawn under varying environments.
Attempt to use SAML with mobile applications? Pain. Otherwise logging in user with OAuth and without OIDC? Missing identity data. Just using SMS codes to submit high-value accounts? Phishable.
Security Pitfalls (and How Modern Protocols Break Them).
All authentication schemes are prone to attack:
Phishing is working against the password and OTPs since the user can be deceived into providing them on the counterfeit websites. Origin binding prevents this, where credentialing is only accepted on the legit out of domain.
In token theft, the access tokens are either stored in a browser local storage or they are leaked in logs. Resolution There is a short lifespan of tokens in secure cookies, which is added to OAuth flows using PKCE and a consideration of binding tokens to particular TLS connections using mTLS or DPoP should be implemented.
Cookie-based session attacks are such as fixation or hijacking. SameSite attributes of cookies developed in modernity can be helpful, but sites should apply them properly.
Actual breaches are caused by protocol misconfiguration: SAML signature validation is not present, in both OAuth and Saml the redirecturi is not properly checked. These details are captured in API authentication best practices and the trend is evident, frameworks and libraries can help avoid foot-guns.
The takeaway? Security does not only dwell on the correct protocol. It is about doing it right, and this consists in being aware of frequent attacks and mitigation of those attacks.
The Hybrid Reality: Living in Between the Legacy and Modern.
The thing that no one tells you about is that the majority of organizations lack an authentic clean authentication strategy. They have:
- Windows domain Kerberos logins.
- SaaS apps that use SAML must have S/aaS apps.
- OAuth/OIDC for newer web apps
- VPN using EAP-TLS
- Un-authenticated internal applications that are barely used.
- A pilot test involving passkeys.
That’s normal. Migration takes years.
The practical approach? Migrate the new development to a standard of OIDC with PKCE, begin integrating WebAuthn with high-value accounts, and continue relying on existing integrations of SAML/Kerberos until they can be replaced.
The worth of perfections in architecture is insignificant compared to what each piece is and why it is created.
Next in Line: Continuous and Risk-Based Authentication.
Identification procedures and schemes are not fixed. Current trends:
Risk-adaptive authentication is adaptable authentication according to the context. Accessing your weekly use device and location? Quick verification. Accessing suddenly but in a new country? Other qualities are necessary.
Constant authentication does not only verify identity upon authentication. It tracks detection of compromised accounts on accounts that have successfully been authenticated by tracking device signals, patterns of behavior and history of a session (Gural 2006).
Decentralized proposes experiments where users manage their credentials with verifiable credentials and DIDs, this is still young and unproven.
Security Hardware-based security augments authentication with device TPMs, Secure Enclaves and platform authenticators ensuring that keys are more difficult to read or duplicate.
These are not substituting the existing protocols. They’re adding layers on top.
Where to Start: Practical Next Steps
The authentication scenario is not very clean as it has developed during decades to address various issues. There is no one including all the protocols.
For learning:
Begin at the mental paradigm: authentication (who is you) vs. authorization (what you can access) vs. federation (proving from one system to another).
Then construct: Build a hands-on: create an OAuth/OIDC authentication flow that uses a cloud provider such as Auth0 or Okta. understand how tokens are used, what there is in each and where things may malfunction.
Install WebAuthn in anMIS test app. Create a passkey, went to different devices, and know why it is not easy to phish.
For implementation:
Take advantage of already developed libraries and structures. Never code your configure ceia own OAuth Objective or JWT validation- utilise wrestle-proposed scripts.
Migration to OIDC of newly-created web applications. Only consider SAML when it is necessary to the enterprise customer.
Beginning to consider multi-factor authentication a standard, and WebAuthn a high-security choice.
Keep your tokens safely: HTTP-only cookies that are generated by the server side are better than cookies stored on the client.
It is not really about learning all the protocols at once. It’s creating a mental model that works so the first thing that they say about DPoP, mTLS or FIDO2 is something that you can understand its position and its significance.
The Eventual Lesson: Content Makes the Difference.
The reason why authentication methods and protocols exist is that people need various contexts to satisfy different needs. Wi-Fi networks need EAP. Enterprise apps need SAML. Mobile apps need OAuth. WebAuthn is required in high security situations.
This perplexity is caused by the attempt to use one solution in all situations or the inability to comprehend what problem each of the protocols should resolve.
Passwords are not disappearing tomorrow but it is apparent that passwordless is the new way to go. SAML is not dead, however OIDC is simpler to stacks in the present time. OAuth is beautiful in terms of its authorization though it requires OIDC in authentication.
This landscape requires one to know when what is needed- and why organizations do find themselves operating multiple protocols at the same time. That’s not dysfunction. And this is how the real world functions.
Read:
How Apple Actually Forces iPhone Upgrades (And How to Push Back)
I’m a technology writer with a passion for AI and digital marketing. I create engaging and useful content that bridges the gap between complex technology concepts and digital technologies. My writing makes the process easy and curious. and encourage participation I continue to research innovation and technology. Let’s connect and talk technology!